Connect Your Smart Gadgets: How To SSH To IoT Devices Safely
Getting your smart home gadgets or other internet-connected little machines to do exactly what you want, when you want, often means getting a bit closer to their inner workings. That, is that, where a method called Secure Shell, or SSH, comes into play. It’s like having a secret, protected line directly to your tiny computer, letting you give it commands and see what it's doing, no matter where you are.
Think about it, you have these small, smart devices scattered around, maybe a tiny computer running your garden's watering system, or a camera watching your pet. You might need to update its software, check its logs, or even tell it to do something new. Doing this from afar, in a way that keeps your information private and safe from others, is pretty important, you know?
This guide will walk you through the steps to get connected, making sure your communication stays private. We'll cover what SSH is, how to set things up, and even how to move files around. So, let's get your IoT device talking to you, securely, shall we?
Table of Contents
- What is SSH and Why Does it Matter for IoT?
- Getting Your IoT Device Ready for SSH
- Generating and Using SSH Keys
- Connecting to Your IoT Device via SSH
- Transferring Files with SCP
- Automating Commands with SSH
- Keeping Your IoT SSH Connection Safe
- Frequently Asked Questions About SSH to IoT Devices
What is SSH and Why Does it Matter for IoT?
SSH, which stands for Secure Shell, is a really clever way to get into another computer over a network. It makes sure that whatever you send back and forth, like commands or files, stays private and can't be seen by others. This is super important for tiny internet devices because they often hold important settings or data, and you definitely want to keep that safe, you know?
Many places that handle lots of computer data, like big server rooms or even just your local business, use SSH. It's a standard tool for keeping things secure when you're working with machines that are not right in front of you. It's how people manage systems and move data around without worrying too much about prying eyes, which is pretty cool.
The Secure Shell Protocol Explained
The SSH protocol is basically a set of rules for making a secure login from one computer to another. It's what allows you to, say, use your laptop to tell your smart thermostat to change its temperature settings, but in a way that no one else can listen in or mess with the command. It offers different ways to prove you are who you say you are, making it very strong for security, as a matter of fact.
This method of secure communication was first thought up by Tatu Ylonen, and then later on, the OpenBSD folks really helped it grow. It's a widely used system, and that's because it does a very good job of keeping things safe. When you see something like `ssh://` at the start of a link, it's telling you that the connection will be using this secure way of talking, which is quite helpful.
Host Keys and Secure Connections
When you connect using SSH, every computer you connect to has a special code, a sort of unique fingerprint, called a host key. Your computer, the one you're connecting from, remembers this key for that specific machine. This helps make sure you're always connecting to the right device and not some imposter trying to trick you, which is a big deal for security, really.
If that host key ever changes unexpectedly, your computer will give you a warning. This is a good thing, because it could mean someone is trying to pretend to be your IoT device. For instance, if you restart your smart gadget or update its system, the host key might change. If you see a message about a changed host key, it's a good idea to double-check things, just to be on the safe side, you know?
Getting Your IoT Device Ready for SSH
Before you can start sending commands to your IoT device, you need to make sure it's set up to listen for SSH connections. This often means turning on a specific service on the device itself. Most tiny computers that are designed for projects, like a Raspberry Pi, come with the ability to use SSH, but you might need to flip a switch to activate it, so.
The exact steps for getting your device ready can vary a bit depending on what kind of gadget you have. Some might have a simple setting in their setup menu, while others might need you to run a command or two directly on the device with a keyboard and screen attached first. It's usually not too hard, though, and definitely worth the effort for the control you get.
Enabling SSH on Your Device
For many popular IoT platforms, enabling SSH is a pretty straightforward process. For example, on a Raspberry Pi, you might use the `raspi-config` tool, which gives you a menu to turn on the SSH server. Other devices might have a web interface where you can tick a box. The main idea is to get the device to start listening for incoming SSH requests, you know?
If your device runs a version of Linux, you'll likely need to install an SSH server package, like OpenSSH. This is a common step, and usually involves a simple command like `sudo apt-get install openssh-server` if you're using a Debian-based system. Once it's installed, you'll want to make sure it starts up automatically when the device powers on, too it's almost.
Network Setup Considerations
Your IoT device needs to be on the same network as the computer you're connecting from, or you'll need to set up some network rules to let the connection through. This often means knowing your device's IP address. You can usually find this by checking your router's connected devices list or by running a command on the device itself, like `ip a` or `ifconfig`, you know?
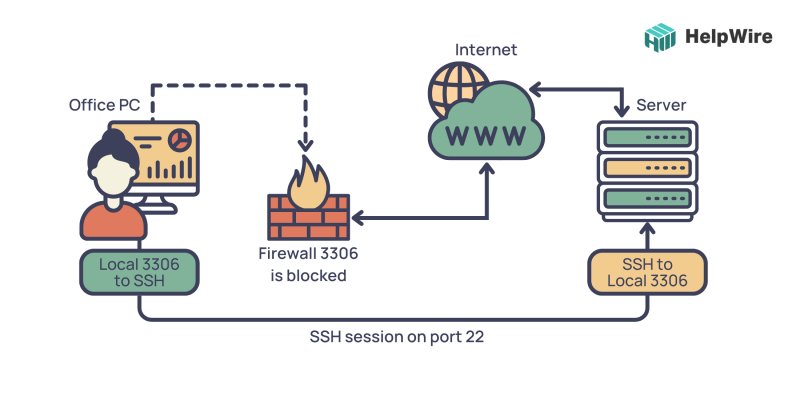
If you plan to connect to your IoT device from outside your home network, things get a little more involved. You might need to set up something called "port forwarding" on your home router. This tells your router to send SSH requests from the internet directly to your IoT device. Just be careful with this, as it does open up a door to your home network, so it's a bit more advanced.
Generating and Using SSH Keys
Using SSH keys is a much safer way to connect than using just a password. Instead of typing in a password every time, you use a pair of digital keys: one private and one public. Your private key stays on your computer, very safe, and your public key goes onto the IoT device. When you try to connect, these keys do a secret handshake to prove it's really you, which is a pretty clever system, actually.
Many people run into issues with SSH connections, like when they change a password or move to a new computer. Generating and using keys helps avoid these kinds of problems because the key itself is your way in, not something you have to remember. It's a bit like having a special, unforgeable pass, in a way.
Creating Your Key Pair
To make your SSH key pair, you'll use a tool called `ssh-keygen` on most Linux or macOS computers. You just open your terminal and type `ssh-keygen`. It will ask you where to save the keys and if you want a passphrase. A passphrase adds an extra layer of security to your private key, which is a good idea, you know?
If you're using a Windows computer, you'll likely use a program called PuTTYgen, which comes with PuTTY. It helps you create these key pairs with a few clicks. Once you've made them, you'll have a private key file and a public key file. Remember to keep your private key very safe and never share it with anyone, absolutely not.
Adding Your Public Key to the IoT Device
Once you have your public key, you need to put it on your IoT device. The simplest way for many Linux-based devices is to use the `ssh-copy-id` command. You just type `ssh-copy-id user@your_iot_device_ip`, and it does all the work for you. It copies your public key to the correct spot on the device, so.
If `ssh-copy-id` isn't available or doesn't work, you can copy the public key manually. You'll need to open your public key file, which usually ends in `.pub`, copy its contents, and then paste it into a file called `authorized_keys` inside the `.ssh` folder in the user's home directory on your IoT device. Make sure the permissions on that folder and file are set correctly for security, that is that.
Managing Multiple SSH Keys
Sometimes, you might need to use different SSH keys for different purposes. For instance, you might have one key for your personal IoT projects and another for connecting to a work server or a specific proxy server. You can tell SSH which key to use with the `-i` option, like `ssh -i ~/.ssh/my_special_key user@device_ip`, which is pretty handy.
You can also set up a special configuration file on your computer, usually at `~/.ssh/config`. In this file, you can give your IoT devices short names and tell SSH which key to use for each one. This makes connecting much easier, as you can just type `ssh myiotdevice` instead of a long command with the IP address and key path, which is quite convenient, you know?
Connecting to Your IoT Device via SSH
With your IoT device ready and your SSH keys in place, you're all set to make that first connection. It's a pretty exciting moment, like opening a direct line to your little gadget. The basic command is quite simple, and once you get the hang of it, you'll be able to connect to any of your devices with ease, really.
You might have seen messages about SSH when doing other things, like working with code repositories. For example, if you're pulling code from a service like GitLab, you're connecting via SSH, which is why you might see messages about the SSH protocol. It's the same underlying technology, just used for different purposes, more or less.
Basic SSH Command Usage
To connect from a Linux or macOS computer, open your terminal and type `ssh username@ip_address_of_your_iot_device`. Replace `username` with the user account on your IoT device (often `pi` for a Raspberry Pi) and `ip_address_of_your_iot_device` with its network address. If everything is set up right, you'll be prompted for a password (if you're not using keys) or you'll just connect directly, so.
For example, if your Raspberry Pi's IP address is `192.168.1.100` and the username is `pi`, you'd type `ssh pi@192.168.1.100`. The first time you connect to a new device, your computer will ask you to confirm its host key. Say "yes" to add it to your known hosts list, which is a good practice for security, obviously.
Using PuTTY for Windows Connections
If you're on Windows, a popular program for SSH connections is PuTTY. You can download it easily. Once you have it, open PuTTY, type your IoT device's IP address into the "Host Name (or IP address)" field, and make sure the "Port" is set to 22 (the standard SSH port). Then, click "Open," and a terminal window will pop up, asking for your username and password, you know?
If you're using SSH keys with PuTTY, you'll need to load your private key file (which will be in a `.ppk` format, converted from the `.pem` or other format by PuTTYgen) under "Connection" > "SSH" > "Auth" in the PuTTY configuration. This tells PuTTY to use your key for proving who you are, making the login process smoother and more secure, as a matter of fact.
Handling Connection Issues
Sometimes, things don't go perfectly on the first try. If you get an error like "Connection refused," it often means the SSH server isn't running on your IoT device, or a firewall is blocking the connection. Double-check that SSH is enabled on the device and that your network allows the connection, perhaps, you know?
If you're having trouble with SSH keys, make sure your private key has the correct permissions (usually readable only by you). Also, ensure your public key is correctly placed in the `authorized_keys` file on the IoT device. If you're using a custom key, remember to specify it with the `-i` flag or in your SSH config file. Sometimes, a simple restart of the SSH service on the IoT device can fix things, too it's almost.
Transferring Files with SCP
Once you have an SSH connection working, you can also use a related tool called SCP (Secure Copy Protocol) to move files and even whole folders between your computer and your IoT device. This is incredibly useful for putting new programs on your device or pulling data off it, like logs or sensor readings, you know?
To copy a file from your computer to the IoT device, you'd use a command like `scp /path/to/local/file username@ip_address:/path/to/remote/location`. For example, `scp my_script.py pi@192.168.1.100:/home/pi/scripts/`. If you want to copy an entire folder, you'll need to add the `-r` option, like `scp -r /path/to/local/folder username@ip_address:/path/to/remote/location`, which is pretty neat.
Copying files the other way around, from your IoT device to your local machine, is just as easy. You simply reverse the order of the source and destination. So, `scp username@ip_address:/path/to/remote/file /path/to/local/location`. This flexibility makes managing your IoT projects much simpler, allowing you to work on files from your main computer and then push them to the device, or pull data for analysis, you know?
Automating Commands with SSH
One of the really powerful things about SSH is that you can use it to run commands on your IoT device directly from a script on your main computer. This is super handy for automating tasks, like restarting a service on your device every night or fetching sensor data at regular intervals. You can write a script that handles all these commands for you, you know?
For example, if you're writing a script in Python, you could use a library that lets you run shell commands. You might have lines of code that look like `command = "ssh pi@192.168.1.100 'ls -l /home/pi/data'"` to list files on your device. This makes it possible to build complex systems where your main computer orchestrates many little IoT gadgets, which is quite amazing, you know?
This ability to script commands over SSH is how many developers manage their projects, especially when dealing with lots of tiny machines. If you ever run into issues, like a certain command not working, you can often find solutions in places that discuss Git or other command-line tools, as the underlying SSH principles are the same, in some respects. For instance, sometimes a quick command to fix permissions can sort things out, just like with Git repositories.
![How to Access IoT Devices Remotely with SSH [6 Easy Steps]](https://www.trio.so/blog/wp-content/uploads/2024/10/Access-IoT-Devices-Remotely-Using-SSH.webp)
How to Access IoT Devices Remotely with SSH [6 Easy Steps]

Step-by-step Guide | How to Remotely Connect to IoT Devices via SSH
Control IoT Devices Behind Firewall – Complete Guide