RemoteIoT Behind Router Example: Your Guide To Easy Device Access
Have you ever found yourself wanting to check on your smart home gadgets or a particular sensor while you're away from home? Perhaps you have a security camera or a temperature monitor, and you want to see what's happening without actually being there. This desire for remote access to your Internet of Things (IoT) devices, especially when they're tucked away behind your home or office router, is a very common wish for many people today, you know. It can feel a bit tricky to set up at first, but with the right steps, it's absolutely doable, and it opens up a whole new level of convenience for managing your connected world, in a way.
Getting your IoT devices to talk to you from a distance, past the protective barrier of your router, involves a few clever tricks. Your router, you see, acts like a digital doorman for your local network, keeping outside connections from just waltzing in. While this is great for security, it does mean your smart devices inside need a special pass to communicate with the outside world, so to speak. This guide is all about giving you those passes, showing you practical ways to achieve remote IoT behind router access, basically.
We'll walk through several approaches, from the more straightforward to the slightly more advanced, making sure you understand the upsides and downsides of each. You'll learn about things like telling your router to open a specific door for a device or setting up a secure tunnel. The goal is to make sure your smart gadgets are always within your reach, no matter where you are, and that's pretty neat, honestly. So, let's get your remote IoT behind router example working for you.
Table of Contents
- The Challenge of Connecting IoT Devices Remotely
- Popular Methods for Remote IoT Access
- Keeping Your Remote IoT Secure
- Picking the Best Method for You
- Handling Common Connection Hiccups
- Frequently Asked Questions
- Making Your IoT Devices Work for You
The Challenge of Connecting IoT Devices Remotely
When you're at home, your smart devices, like your smart lights or your thermostat, happily chat with your phone or computer because they are all on the same local network. Your router, that little box with antennas, gives each device a private address, kind of like an internal phone number, so they can find each other. This setup works perfectly for local control, of course.
The problem starts when you leave your home network. Your router, being a good protector, hides all those private internal addresses from the outside world. It uses something called Network Address Translation, or NAT, which basically lets many devices share one public internet address. So, when you're out and about, trying to reach your smart light, the internet only sees your router's public address, not the light's private one. It's like trying to call someone in an apartment building without knowing their apartment number, only the building's address, you know?
This protective barrier, while very good for keeping unwanted visitors out, makes direct remote access a bit of a puzzle. Your router doesn't automatically know which internal device you want to talk to when a request comes in from the internet. It needs specific instructions, a kind of map, to direct that incoming request to the right device inside your network. This is where the various methods for remote IoT behind router examples come into play, offering different ways to draw that map, basically.
- Maplestar Animations
- How Much Does Patience Wolfe Make
- Aditi Mistry Nipples
- Somalia Wasmo
- Remoteiot Device Ssh
Popular Methods for Remote IoT Access
Getting your devices accessible from afar means finding a way to bridge that gap between your home network and the wider internet. There are several popular ways to do this, each with its own set of advantages and things to consider. Let's look at some of the most common and effective methods for achieving remote IoT behind router access, you know, so you can pick what fits your situation best.
Port Forwarding: A Direct Path
Port forwarding is a very common way to let outside traffic reach a specific device inside your network. Think of it like telling your router, "Hey, if someone knocks on this specific door number (a port) from the internet, send them straight to this device's address (IP address) and this specific door number (port) inside my house." It creates a direct, open line, so to speak, from the internet to your chosen IoT device.
Setting it up usually means logging into your router's settings, finding the "Port Forwarding" section, and then entering the public port you want to use, your device's internal IP address, and the internal port your device uses. For instance, if your IoT camera uses port 8080 internally, you might tell your router to forward external port 8080 (or another chosen port like 8081) to your camera's internal IP address on port 8080. It's a pretty direct way to get things done, actually.
While straightforward, port forwarding does come with some security considerations. By opening a specific port, you are creating a potential entry point into your network. It's very important to make sure the device you're forwarding to is completely secure, meaning it has strong passwords, updated firmware, and isn't running any unnecessary services. If not, you could be leaving a door open for unwanted visitors, which is something nobody wants, really.
Virtual Private Networks (VPNs): The Secure Tunnel
A Virtual Private Network, or VPN, offers a much more secure way to access your home network and all your IoT devices from anywhere. Instead of opening individual doors (ports) for each device, a VPN creates a secure, encrypted tunnel directly into your home network. It's like you're physically sitting at home, even if you're thousands of miles away, so you can access everything as if you were local, you know.
There are two main ways to use VPNs for this purpose. You can set up a VPN server directly on your home router, if your router supports it. This is often the most convenient method, as once the VPN connection is made, all your devices inside are accessible. Alternatively, you can run a VPN server on a dedicated computer or a Raspberry Pi inside your network. Both methods essentially let you "dial in" to your home network securely, which is pretty neat.
When you connect to your home VPN from your phone or laptop, your device gets a temporary IP address from your home network's range. This means you can then access all your IoT devices using their private internal IP addresses, just like you would if you were at home. This method is highly recommended for security, as the entire connection is encrypted, and you're not leaving any open ports exposed to the wider internet, which is a big plus, frankly.
Cloud-Based IoT Platforms and Services: The Easy Route
Many modern IoT devices and systems are designed to work with cloud-based platforms, offering a simpler way to manage remote access without needing to mess with router settings. These platforms, like Amazon Web Services (AWS) IoT, Google Cloud IoT Core, or even manufacturer-specific apps, act as a middleman. Your IoT device connects outbound to the cloud service, and then you connect to the same cloud service from your phone or computer, you see.
This approach works because your IoT device initiates the connection to the cloud, rather than waiting for an incoming connection. Since it's an outbound connection, your router typically allows it without any special configuration. The cloud platform then handles the communication between your remote device (your phone) and your IoT gadget. This is why many smart home devices "just work" out of the box for remote control, which is quite convenient, honestly.
While incredibly convenient, relying on cloud services does mean you're trusting a third party with your device's data and control. It's important to choose reputable services and understand their privacy policies. For many users, especially those who prefer ease of use over complete control of their data, this is often the simplest and most user-friendly remote IoT behind router example to get going, basically.
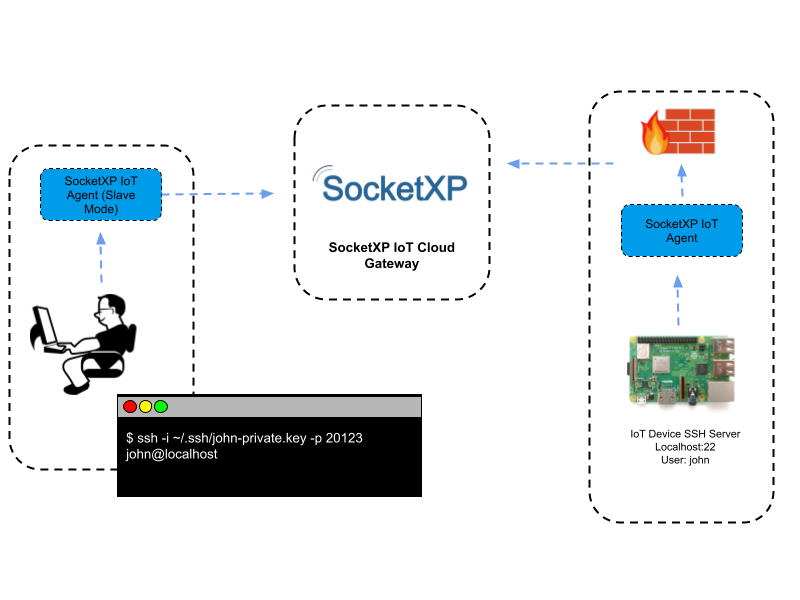
Reverse Proxies and Secure Tunnels for Web Interfaces
For IoT devices that have a web interface (like a smart camera's configuration page or a home automation server), a reverse proxy or a secure tunneling service can be a good option. A reverse proxy sits in front of your device and forwards requests to it, while a secure tunnel creates a secure connection from your internal device to an external server, making it accessible via that server's public address, you know.
Services like Ngrok or Cloudflare Tunnel (formerly Argo Tunnel) create a secure, outbound tunnel from your device or a server on your home network to their cloud infrastructure. They then give you a public URL that you can use to access your internal web interface. This means you don't need to open any ports on your router, as the connection is initiated from inside your network outwards, which is a big security advantage, really.
This method is particularly useful for accessing web-based control panels or dashboards for your IoT setup. It provides a secure way to expose a specific service without exposing your entire network. While some services offer free tiers, more advanced features or higher bandwidth might require a paid subscription, so that's something to keep in mind, too, it's almost.
Universal Plug and Play (UPnP): A Cautionary Tale
Universal Plug and Play, or UPnP, is a feature found on many routers that allows devices on your local network to automatically configure port forwarding rules. In theory, this sounds incredibly convenient for remote IoT behind router access, as devices can just "ask" the router to open the necessary ports without you doing anything manually. Many older smart devices or gaming consoles might try to use UPnP, you see.
However, UPnP is generally considered a significant security risk. Because devices can automatically open ports without user intervention, a malicious piece of software on one of your devices could potentially open a port that lets attackers into your network without your knowledge. It removes the human oversight from the port-opening process, which is quite concerning, frankly.
For this reason, most security experts strongly recommend disabling UPnP on your router and manually configuring any necessary port forwards or using more secure methods like VPNs or cloud services. While it might seem like an easy button, the potential security vulnerabilities far outweigh the convenience for most remote IoT applications, so it's best to avoid it, basically.
Local Mesh Networks and Their Reach
While not directly a remote access method for external connections, understanding local mesh networks is important for a complete remote IoT behind router example. Technologies like Zigbee, Z-Wave, and Thread create their own mesh networks within your home, allowing devices to communicate with each other and extend the range of your smart home hub. This hub then typically connects to your main Wi-Fi network and, in turn, to the internet, you know.
The remote access for these mesh network devices usually happens through the central hub or bridge, which then uses one of the methods discussed above (most often, a cloud-based service) to communicate with your remote app. So, while the mesh itself is local, it's a critical part of how many smart home systems function and ultimately enable remote control, basically.
For example, your Philips Hue lights use a Zigbee mesh network, but you control them remotely through the Hue Bridge, which connects to the internet via Philips' cloud service. This layered approach allows for robust local communication while still providing seamless remote access, which is pretty clever, honestly.
Keeping Your Remote IoT Secure
No matter which method you choose for your remote IoT behind router example, security should always be a top priority. Opening your home network to the outside world, even in a controlled way, introduces potential risks. Taking a few proactive steps can greatly reduce these risks and keep your smart devices and your personal data safe, you know.
Always use strong, unique passwords for all your IoT devices, your router, and any cloud accounts. Default passwords are a huge no-no. Make sure to regularly update the firmware on your router and all your IoT devices. These updates often include critical security patches that fix vulnerabilities. Ignoring them is like leaving your front door unlocked, basically.
Consider network segmentation if you have many IoT devices. This means creating a separate Wi-Fi network or VLAN specifically for your IoT gadgets, isolating them from your main computers and sensitive data. If an IoT device were to be compromised, it would be much harder for an attacker to move from that device to your more important systems. It's a bit more advanced, but it offers a lot of peace of mind, frankly.
Picking the Best Method for You
Deciding on the best remote IoT behind router example really depends on your comfort level with technology, your security needs, and the specific devices you're trying to access. For most people, especially those using off-the-shelf smart home products, cloud-based services are often the simplest way to go. They require minimal setup on your end and typically handle all the complex networking bits, you see.
If you're a bit more tech-savvy and value privacy and control, setting up a VPN server on your router or a dedicated device offers the highest level of security and flexibility. It gives you full access to your entire home network, not just specific devices, through a secure tunnel. This is a very powerful option for those who want to build their own custom smart home solutions, you know.
Port forwarding can work for specific applications but should be used with extreme caution and only for devices that are absolutely secure and regularly updated. It's generally not recommended for beginners due to the potential security implications. Always weigh the convenience against the security risks when making your choice, as that's pretty important, honestly.
Handling Common Connection Hiccups
Even with the best planning, you might run into a few bumps when trying to get your remote IoT behind router example working. One common issue is a dynamic IP address from your internet provider. If your home's public IP address changes, your remote connection might break. Services like Dynamic DNS (DDNS) can help here by linking a consistent hostname to your changing IP address, which is quite useful, you know.
Another frequent problem is incorrect port numbers or IP addresses in your router's settings. Double-check that the internal IP address you've entered for port forwarding matches your device's actual IP address, and that the ports are correct. Firewall settings on your router or even on the IoT device itself can also block connections, so you might need to adjust those too, basically.
If you're using a cloud service and things aren't working, check the device's connection status within the manufacturer's app or web portal. Sometimes, a simple restart of the IoT device or your router can clear up temporary glitches. Patience and methodical troubleshooting are key to getting everything to communicate smoothly from afar, frankly.
Frequently Asked Questions
Here are some common questions people ask about getting remote access to their IoT devices:
Is it safe to open ports on my router for IoT devices?
Opening ports can be safe if done very carefully, but it introduces risks. You must make sure the device receiving the connection is completely secure, updated, and uses strong passwords. For better security, a VPN or cloud-based service is usually a better choice, you know, as they offer more protection against unwanted access.
What is the easiest way to access my smart home devices when I'm not home?
For most smart home devices, the easiest way is usually through their manufacturer's official app or cloud service. These systems are designed to handle the remote connection automatically, without you needing to change router settings. It's often the most straightforward remote IoT behind router example for everyday users, basically.
Can I use a VPN to access all my devices at home, not just IoT?
Yes, absolutely! Setting up a VPN server on your home router or a dedicated computer lets you securely access your entire home network, including all your computers, network drives, and any IoT devices, as if you were physically there. It's a very versatile and secure solution, which is pretty powerful, honestly. Learn more about VPNs on our site.
Making Your IoT Devices Work for You
Getting your remote IoT behind router example up and running truly transforms how you interact with your smart home or remote sensors. It moves your devices from being just "smart" to being genuinely accessible and useful, no matter where life takes you. Whether you're keeping an eye on things, adjusting settings, or just checking in, having that remote connection brings a lot of peace of mind, you know.
Remember to always prioritize security in your setup. A connected home is a convenient home, but a secure connected home is a smart home. Take the time to understand the methods, choose the one that fits your needs and technical comfort, and always keep your devices and network protected. We hope this guide helps you connect with your devices more freely, and that's pretty cool, honestly. You can also link to this page for more tips on network security.

Best Remote IoT Setup Behind Router With Raspberry Pi
Remote IoT Behind Router Example Raspberry Pi: A Comprehensive Guide

RemoteIoT Behind Router Example In Raspberry Pi: A Comprehensive Guide